2025 New SY0-501 Exam Dumps with PDF and VCE Free: https://www.2passeasy.com/dumps/SY0-501/
It is impossible to pass CompTIA SY0-501 exam without any help in the short term. Come to us soon and find the most advanced, correct and guaranteed . You will get a surprising result by our .
Free demo questions for CompTIA SY0-501 Exam Dumps Below:
NEW QUESTION 1
Which of the following authentication concepts is a gait analysis MOST closely associated?
- A. Somewhere you are
- B. Something you are
- C. Something you do
- D. Something you know
Answer: C
NEW QUESTION 2
The computer resource center issued smartphones to all first-level and above managers. The managers have the ability to install mobile tools. Which of the following tools should be implemented to control the types of tools the managers install?
- A. Download manager
- B. Content manager
- C. Segmentation manager
- D. Application manager
Answer: D
NEW QUESTION 3
A vice president at a manufacturing organization is concerned about desktops being connected to the network. Employees need to log onto the desktops' local account to verify that a product is being created within specifications; otherwise, the desktops should be as isolated as possible. Which of the following is the BEST way to accomplish this?
- A. Put the desktops in the DMZ.
- B. Create a separate VLAN for the desktops.
- C. Air gap the desktops.
- D. Join the desktops to an ad-hoc network.
Answer: C
NEW QUESTION 4
An incident responder receives a call from a user who reports a computer is exhibiting symptoms consistent with a malware infection. Which of the following steps should the responder perform NEXT?
- A. Capture and document necessary information to assist in the response.
- B. Request the user capture and provide a screenshot or recording of the symptoms.
- C. Use a remote desktop client to collect and analyze the malware in real time.
- D. Ask the user to back up files for later recovery.
Answer: A
NEW QUESTION 5
A technician is configuring a wireless guest network. After applying the most recent changes the technician finds the new devices can no longer find the wireless network by name but existing devices are still able to use the wireless network.
Which of the following security measures did the technician MOST likely implement to cause this Scenario?
- A. Deactivation of SSID broadcast
- B. Reduction of WAP signal output power
- C. Activation of 802.1X with RADIUS
- D. Implementation of MAC filtering
- E. Beacon interval was decreased
Answer: A
NEW QUESTION 6
A new security policy in an organization requires that all file transfers within the organization be completed using applications that provide secure transfer. Currently, the organization uses FTP and HTTP to transfer files. Which of the following should the organization implement in order to be compliant with the new policy?
- A. Replace FTP with SFTP and replace HTTP with TLS
- B. Replace FTP with FTPS and replaces HTTP with TFTP
- C. Replace FTP with SFTP and replace HTTP with Telnet
- D. Replace FTP with FTPS and replaces HTTP with IPSec
Answer: A
NEW QUESTION 7
A security analyst has received the following alert snippet from the HIDS appliance: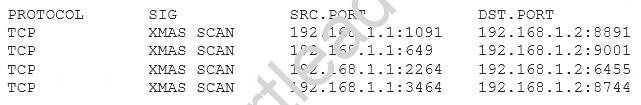
Given the above logs, which of the following is the cause of the attack?
- A. The TCP ports on destination are all open
- B. FIN, URG, and PSH flags are set in the packet header
- C. TCP MSS is configured improperly
- D. There is improper Layer 2 segmentation
Answer: B
NEW QUESTION 8
A company determines that it is prohibitively expensive to become compliant with new credit card regulations. Instead, the company decides to purchase insurance to cover the cost of any potential loss. Which of the following is the company doing?
- A. Transferring the risk
- B. Accepting the risk
- C. Avoiding the risk
- D. Migrating the risk
Answer: A
NEW QUESTION 9
A malicious system continuously sends an extremely large number of SYN packets to a server. Which of the following BEST describes the resulting effect?
- A. The server will be unable to server clients due to lack of bandwidth
- B. The server's firewall will be unable to effectively filter traffic due to the amount of data transmitted
- C. The server will crash when trying to reassemble all the fragmented packets
- D. The server will exhaust its memory maintaining half-open connections
Answer: D
NEW QUESTION 10
Joe, a salesman, was assigned to a new project that requires him to travel to a client site. While waiting for a flight, Joe, decides to connect to the airport wireless network without connecting to a VPN, and the sends confidential emails to fellow colleagues. A few days later, the company experiences a data breach. Upon investigation, the company learns Joe's emails were intercepted. Which of the following MOST likely caused the data breach?
- A. Policy violation
- B. Social engineering
- C. Insider threat
- D. Zero-day attack
Answer: A
NEW QUESTION 11
A security administrator determined that users within the company are installing unapproved software. Company policy dictates that only certain applications may be installed or ran on the user's computers without exception. Which of the following should the administrator do to prevent all unapproved software from running on the user's computer?
- A. Deploy antivirus software and configure it to detect and remove pirated software
- B. Configure the firewall to prevent the downloading of executable files
- C. Create an application whitelist and use OS controls to enforce it
- D. Prevent users from running as administrator so they cannot install software.
Answer: C
NEW QUESTION 12
The SSID broadcast for a wireless router has been disabled but a network administrator notices that unauthorized users are accessing the wireless network. The administer has determined that attackers are still able to detect the presence of the wireless network despite the fact the SSID has been disabled. Which of the following would further obscure the presence of the wireless network?
- A. Upgrade the encryption to WPA or WPA2
- B. Create a non-zero length SSID for the wireless router
- C. Reroute wireless users to a honeypot
- D. Disable responses to a broadcast probe request
Answer: D
NEW QUESTION 13
A security engineer is configuring a wireless network with EAP-TLS. Which of the following activities is a requirement for this configuration?
- A. Setting up a TACACS+ server
- B. Configuring federation between authentication servers
- C. Enabling TOTP
- D. Deploying certificates to endpoint devices
Answer: D
NEW QUESTION 14
An organization requires users to provide their fingerprints to access an application. To improve security, the application developers intend to implement multifactor authentication. Which of the following should be implemented?
- A. Use a camera for facial recognition
- B. Have users sign their name naturally
- C. Require a palm geometry scan
- D. Implement iris recognition
Answer: B
NEW QUESTION 15
A computer emergency response team is called at midnight to investigate a case in which a mail server was restarted. After an initial investigation, it was discovered that email is being exfiltrated through an active connection. Which of the following is the NEXT step the team should take?
- A. Identify the source of the active connection
- B. Perform eradication of active connection and recover
- C. Performance containment procedure by disconnecting the server
- D. Format the server and restore its initial configuration
Answer: A
NEW QUESTION 16
After attempting to harden a web server, a security analyst needs to determine if an application remains vulnerable to SQL injection attacks. Which of the following would BEST assist the analyst in making this determination?
- A. tracert
- B. Fuzzer
- C. nslookup
- D. Nmap
- E. netcat
Answer: B
Recommend!! Get the Full SY0-501 dumps in VCE and PDF From Certifytools, Welcome to Download: https://www.certifytools.com/SY0-501-exam.html (New 540 Q&As Version)