2025 New SY0-501 Exam Dumps with PDF and VCE Free: https://www.2passeasy.com/dumps/SY0-501/
It is impossible to pass CompTIA SY0-501 exam without any help in the short term. Come to us soon and find the most advanced, correct and guaranteed . You will get a surprising result by our .
Check SY0-501 free dumps before getting the full version:
NEW QUESTION 1
You have been tasked with designing a security plan for your company. Drag and drop the appropriate security controls on the floor plan.
Instructions: All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.
Answer:
Explanation: Cable locks - Adding a cable lock between a laptop and a desk prevents someone from picking it up and
walking away
Proximity badge + reader
Safe is a hardware/physical security measure
Mantrap can be used to control access to sensitive areas. CCTV can be used as video surveillance. Biometric reader can be used to control and prevent unauthorized access. Locking cabinets can be used to
protect backup media, documentation and other physical artefacts.
NEW QUESTION 2
A security analyst has set up a network tap to monitor network traffic for vulnerabilities. Which of the following techniques would BEST describe the approach the analyst has taken?
- A. Compliance scanning
- B. Credentialed scanning
- C. Passive vulnerability scanning
- D. Port scanning
Answer: D
NEW QUESTION 3
A software development manager is taking over an existing software development project. The team currently suffers from poor communication due to a long delay between requirements documentation and feature delivery. This gap is resulting in an above average number of security-related bugs making it into production. Which of the following development methodologies is the team MOST likely using now?
- A. Agile
- B. Waterfall
- C. Scrum
- D. Spiral
Answer: B
NEW QUESTION 4
Which of the following is an important step to take BEFORE moving any installation packages from a test environment to production?
- A. Roll back changes in the test environment
- B. Verify the hashes of files
- C. Archive and compress the files
- D. Update the secure baseline
Answer: B
NEW QUESTION 5
A software developer is concerned about DLL hijacking in an application being written. Which of the following is the MOST viable mitigation measure of this type of attack?
- A. The DLL of each application should be set individually
- B. All calls to different DLLs should be hard-coded in the application
- C. Access to DLLs from the Windows registry should be disabled
- D. The affected DLLs should be renamed to avoid future hijacking
Answer: B
NEW QUESTION 6
A security analyst is investigating a security breach. Upon inspection of the audit an access logs, the analyst notices the host was accessed and the /etc/passwd file was modified with a new entry for username “gotcha” and user ID of 0. Which of the following are the MOST likely attack vector and tool the analyst should use to determine if the attack is still ongoing? (Select TWO)
- A. Logic bomb
- B. Backdoor
- C. Keylogger
- D. Netstat
- E. Tracert
- F. Ping
Answer: BD
NEW QUESTION 7
An administrator is configuring access to information located on a network file server named “Bowman”. The files are located in a folder named “BalkFiles”. The files are only for use by the “Matthews” division and should be read-only. The security policy requires permissions for shares to be managed at the file system layer and also requires those permissions to be set according to a least privilege model. Security policy for this data type also dictates that administrator-level accounts on the system have full access to the files.
The administrator configures the file share according to the following table: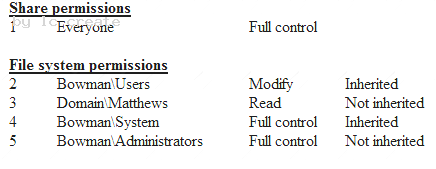
Which of the following rows has been misconfigured?
- A. Row 1
- B. Row 2
- C. Row 3
- D. Row 4
- E. Row 5
Answer: D
NEW QUESTION 8
Which of the following is the LEAST secure hashing algorithm?
- A. SHA1
- B. RIPEMD
- C. MD5
- D. DES
Answer: C
NEW QUESTION 9
Which of the following is an asymmetric function that generates a new and separate key every time it runs?
- A. RSA
- B. DSA
- C. DHE
- D. HMAC
- E. PBKDF2
Answer: C
NEW QUESTION 10
Which of the following vulnerability types would the type of hacker known as a script kiddie be MOST dangerous against?
- A. Passwords written on the bottom of a keyboard
- B. Unpatched exploitable Internet-facing services
- C. Unencrypted backup tapes
- D. Misplaced hardware token
Answer: B
NEW QUESTION 11
Which of the following AES modes of operation provide authentication? (Select two.)
- A. CCM
- B. CBC
- C. GCM
- D. DSA
- E. CFB
Answer: AC
NEW QUESTION 12
A penetration tester has written an application that performs a bit-by-bit XOR 0xFF operation on binaries prior to transmission over untrusted mediA. Which of the following BEST describes the action performed by this type of application?
- A. Hashing
- B. Key exchange
- C. Encryption
- D. Obfusication
Answer: D
NEW QUESTION 13
The Chief Technology Officer (CTO) of a company, Ann, is putting together a hardware budget for the next 10 years. She is asking for the average lifespan of each hardware device so that she is able to calculate when she will have to replace each device.
Which of the following categories BEST describes what she is looking for?
- A. ALE
- B. MTTR
- C. MTBF
- D. MTTF
Answer: D
NEW QUESTION 14
A security administrator has been assigned to review the security posture of the standard corporate system image for virtual machines. The security administrator conducts a thorough review of the system logs, installation procedures, and network configuration of the VM image. Upon reviewing the access logs and user accounts, the security administrator determines that several accounts will not be used in production.
Which of the following would correct the deficiencies?
- A. Mandatory access controls
- B. Disable remote login
- C. Host hardening
- D. Disabling services
Answer: C
NEW QUESTION 15
Although a web enabled application appears to only allow letters in the comment field of a web form, malicious user was able to carry a SQL injection attack by sending special characters through the web comment field.
Which of the following has the application programmer failed to implement?
- A. Revision control system
- B. Client side exception handling
- C. Server side validation
- D. Server hardening
Answer: C
NEW QUESTION 16
While reviewing the monthly internet usage it is noted that there is a large spike in traffic classified as "unknown" and does not appear to be within the bounds of the organizations Acceptable Use Policy.
Which of the following tool or technology would work BEST for obtaining more information on this traffic?
- A. Firewall logs
- B. IDS logs
- C. Increased spam filtering
- D. Protocol analyzer
Answer: B
P.S. Dumpscollection now are offering 100% pass ensure SY0-501 dumps! All SY0-501 exam questions have been updated with correct answers: http://www.dumpscollection.net/dumps/SY0-501/ (540 New Questions)