2025 New SY0-501 Exam Dumps with PDF and VCE Free: https://www.2passeasy.com/dumps/SY0-501/
It is more faster and easier to pass the by using . Immediate access to the and find the same core area with professionally verified answers, then PASS your exam with a high score now.
Check SY0-501 free dumps before getting the full version:
NEW QUESTION 1
Which of the following is the proper order for logging a user into a system from the first step to the last step?
- A. Identification, authentication, authorization
- B. Identification, authorization, authentication
- C. Authentication, identification, authorization
- D. Authentication, identification, authorization
- E. Authorization, identification, authentication
Answer: A
NEW QUESTION 2
A recent internal audit is forcing a company to review each internal business unit's VMs because the cluster they are installed on is in danger of running out of computer resources. Which of the following vulnerabilities exist?
- A. Buffer overflow
- B. End-of-life systems
- C. System sprawl
- D. Weak configuration
Answer: C
NEW QUESTION 3
Joe is exchanging encrypted email with another party. Joe encrypts the initial email with a key. When Joe receives a response, he is unable to decrypt the response with the same key he used initially. Which of the following would explain the situation?
- A. An ephemeral key was used for one of the messages
- B. A stream cipher was used for the initial email; a block cipher was used for the reply
- C. Out-of-band key exchange has taken place
- D. Asymmetric encryption is being used
Answer: D
Explanation: Asymmetric algorithms use two keys to encrypt and decrypt datA. These asymmetric keys are referred to as the public key and the private key. The sender uses the public key to encrypt a message, and the receiver uses the private key to decrypt the message; what one key does, the other one undoes.
NEW QUESTION 4
A security auditor is putting together a report for the Chief Executive Officer (CEO) on personnel security and its impact on the security posture of the whole organization. Which of the following would be the MOST important factor to consider when it comes to personnel security?
- A. Insider threats
- B. Privilege escalation
- C. Hacktivist
- D. Phishing through social media
- E. Corporate espionage
Answer: A
NEW QUESTION 5
A home invasion occurred recently in which an intruder compromised a home network and accessed a WiFIenabled baby monitor while the baby's parents were sleeping.
Which of the following BEST describes how the intruder accessed the monitor?
- A. Outdated antivirus
- B. WiFi signal strength
- C. Social engineering
- D. Default configuration
Answer: D
NEW QUESTION 6
An attacker captures the encrypted communication between two parties for a week, but is unable to decrypt the messages. The attacker then compromises the session key during one exchange and successfully compromises a single message. The attacker plans to use this key to decrypt previously captured and future communications, but is unable to. This is because the encryption scheme in use adheres to:
- A. Asymmetric encryption
- B. Out-of-band key exchange
- C. Perfect forward secrecy
- D. Secure key escrow
Answer: C
NEW QUESTION 7
Two users need to securely share encrypted files via email. Company policy prohibits users from sharing credentials or exchanging encryption keys. Which of the following can be implemented to enable users to share encrypted data while abiding by company policies?
- A. Key escrow
- B. Digital signatures
- C. PKI
- D. Hashing
Answer: B
NEW QUESTION 8
A security administrator is given the security and availability profiles for servers that are being deployed. Match each RAID type with the correct configuration and MINIMUM number of drives.
Match each RAID type with the correct configuration and MINIMUM number of drives. Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:
Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions: All drive definitions can be dragged as many times as necessary
All drive definitions can be dragged as many times as necessary Not all placeholders may be filled in the RAID configuration boxes
Not all placeholders may be filled in the RAID configuration boxes If parity is required, please select the appropriate number of parity checkboxes
If parity is required, please select the appropriate number of parity checkboxes  Server profiles may be dragged only once
Server profiles may be dragged only once
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.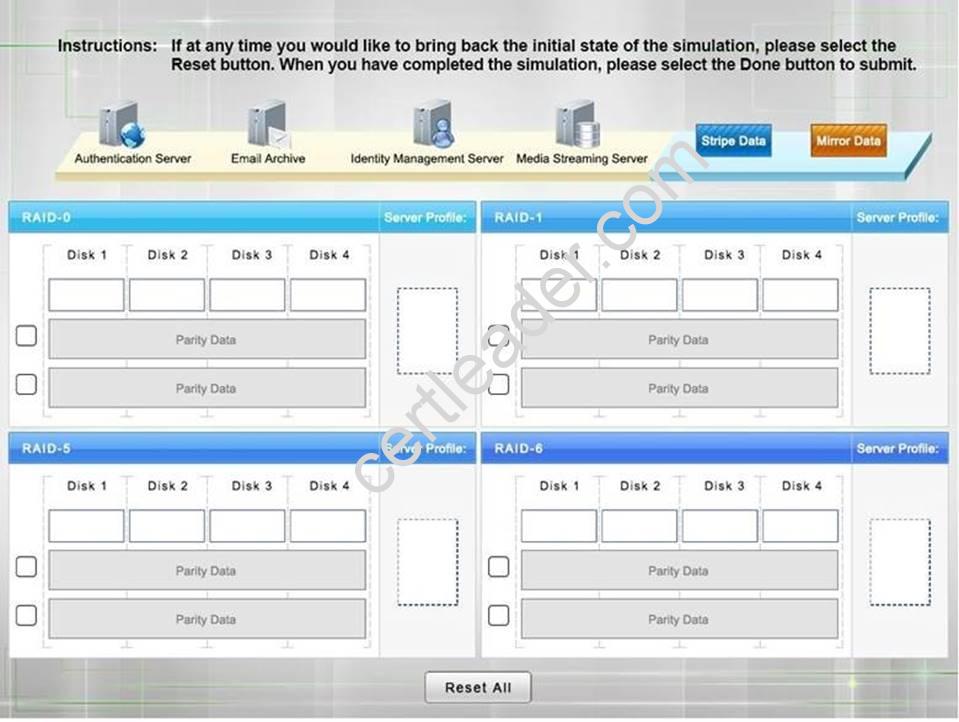
Answer:
Explanation: RAID-0 is known as striping. It is not a fault tolerant solution but does improve disk performance for read/write operations. Striping requires a minimum of two disks and does not use parity.
RAID-0 can be used where performance is required over fault tolerance, such as a media streaming server. RAID-1 is known as mirroring because the same data is written to two disks so that the two disks have
identical data. This is a fault tolerant solution that halves the storage space. A minimum of two disks are used in mirroring and does not use parity. RAID-1 can be used where fault tolerance is required over performance, such as on an authentication server. RAID-5 is a fault tolerant solution that uses parity and striping. A minimum of three disks are required for RAID-5 with one disk's worth of space being used for parity information. However, the parity information is distributed across all the disks. RAID-5 can recover from a sing disk failure.
RAID-6 is a fault tolerant solution that uses dual parity and striping. A minimum of four disks are required for RAID-6. Dual parity allows RAID-6 to recover from the simultaneous failure of up to two disks. Critical data should be stored on a RAID-6 system.
http://www.adaptec.com/en-us/solutions/raid_levels.html
NEW QUESTION 9
New magnetic locks were ordered for an entire building. In accordance with company policy, employee safety is the top priority. In case of a fire where electricity is cut, which of the following should be taken into consideration when installing the new locks?
- A. Fail safe
- B. Fault tolerance
- C. Fail secure
- D. Redundancy
Answer: A
NEW QUESTION 10
An application team is performing a load-balancing test for a critical application during off-hours and has requested access to the load balancer to review which servers are up without having the administrator on call.
The security analyst is hesitant to give the application team full access due to other critical applications running on the load balancer. Which of the following is the BEST solution for security analyst to process the request?
- A. Give the application team administrator access during off-hours.
- B. Disable other critical applications before granting the team access.
- C. Give the application team read-only access.
- D. Share the account with the application team.
Answer: C
NEW QUESTION 11
Ann, a security administrator, wants to ensure credentials are encrypted in transit when implementing a RADIUS server for SSO. Which of the following are needed given these requirements? (Select TWO)
- A. Public key
- B. Shared key
- C. Elliptic curve
- D. MD5
- E. Private key
- F. DES
Answer: AE
NEW QUESTION 12
Which of the following would allow for the QUICKEST restoration of a server into a warm recovery site in a case in which server data mirroring is not enabled?
- A. Full backup
- B. Incremental backup
- C. Differential backup
- D. Snapshot
Answer: C
NEW QUESTION 13
An organization is using a tool to perform a source code review. Which of the following describes the case in which the tool incorrectly identifies the vulnerability?
- A. False negative
- B. True negative
- C. False positive
- D. True positive
Answer: C
NEW QUESTION 14
Ann is the IS manager for several new systems in which the classification of the systems' data are being decided. She is trying to determine the sensitivity level of the data being processed. Which of the following people should she consult to determine the data classification?
- A. Steward
- B. Custodian
- C. User
- D. Owner
Answer: D
NEW QUESTION 15
Systems administrator and key support staff come together to simulate a hypothetical interruption of service. The team updates the disaster recovery processes and documentation after meeting. Which of the following
describes the team's efforts?
- A. Business impact analysis
- B. Continuity of operation
- C. Tabletop exercise
- D. Order of restoration
Answer: C
NEW QUESTION 16
Multiple employees receive an email with a malicious attachment that begins to encrypt their hard drives and mapped shares on their devices when it is opened. The network and security teams perform the following actions: Shut down all network shares.
Shut down all network shares. Run an email search identifying all employees who received the malicious message.
Run an email search identifying all employees who received the malicious message.  Reimage all devices belonging to users who opened the attachment.
Reimage all devices belonging to users who opened the attachment.
Next, the teams want to re-enable the network shares. Which of the following BEST describes this phase of the incident response process?
- A. Eradication
- B. Containment
- C. Recovery
- D. Lessons learned
Answer: C
Recommend!! Get the Full SY0-501 dumps in VCE and PDF From Dumpscollection, Welcome to Download: http://www.dumpscollection.net/dumps/SY0-501/ (New 540 Q&As Version)