2025 New SY0-501 Exam Dumps with PDF and VCE Free: https://www.2passeasy.com/dumps/SY0-501/
We provide in two formats. Download PDF & Practice Tests. Pass CompTIA SY0-501 Exam quickly & easily. The SY0-501 PDF type is available for reading and printing. You can print more and practice many times. With the help of our product and material, you can easily pass the SY0-501 exam.
CompTIA SY0-501 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
After a merger between two companies a security analyst has been asked to ensure that the organization's systems are secured against infiltration by any former employees that were terminated during the transition.
Which of the following actions are MOST appropriate to harden applications against infiltration by former employees? (Select TWO)
- A. Monitor VPN client access
- B. Reduce failed login out settings
- C. Develop and implement updated access control policies
- D. Review and address invalid login attempts
- E. Increase password complexity requirements
- F. Assess and eliminate inactive accounts
Answer: CF
NEW QUESTION 2
An employee uses RDP to connect back to the office network. If RDP is misconfigured, which of the following security exposures would this lead to?
- A. A virus on the administrator's desktop would be able to sniff the administrator's username and password.
- B. Result in an attacker being able to phish the employee's username and password.
- C. A social engineering attack could occur, resulting in the employee's password being extracted.
- D. A man in the middle attack could occur, resulting the employee's username and password being captured.
Answer: D
NEW QUESTION 3
Phishing emails frequently take advantage of high-profile catastrophes reported in the news. Which of the following principles BEST describes the weakness being exploited?
- A. Intimidation
- B. Scarcity
- C. Authority
- D. Social proof
Answer: D
NEW QUESTION 4
A security administrator discovers that an attack has been completed against a node on the corporate network. All available logs were collected and stored.
You must review all network logs to discover the scope of the attack, check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. The environment is a critical production environment; perform the LEAST disruptive actions on the network, while still performing the appropriate incid3nt responses.
Instructions: The web server, database server, IDS, and User PC are clickable. Check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. Not all actions may be used, and order is not important. If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.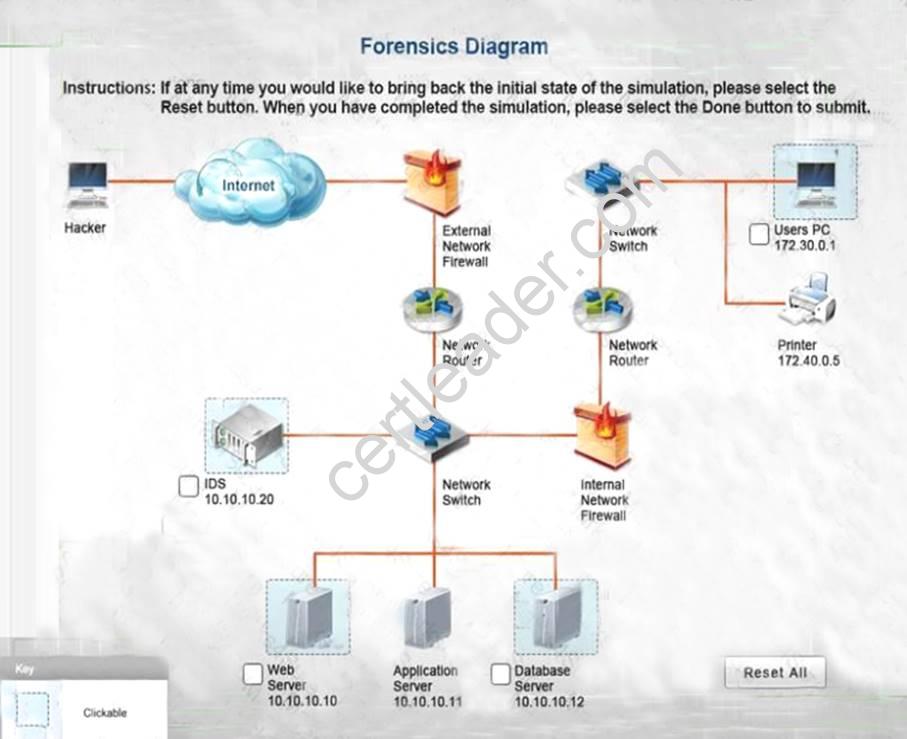
Answer:
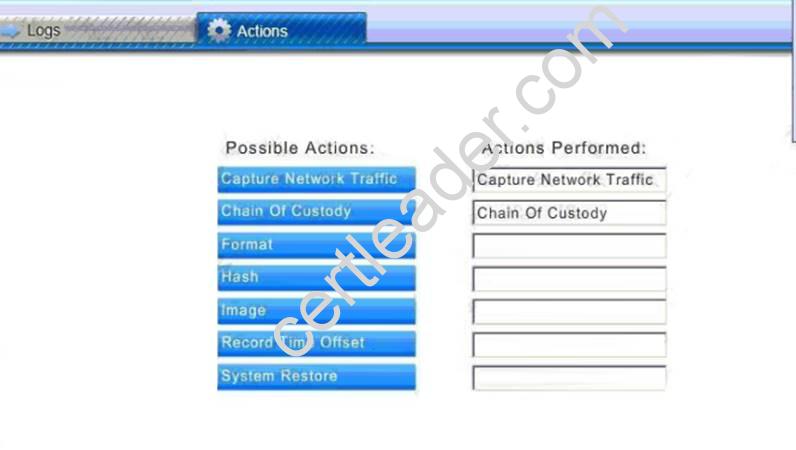
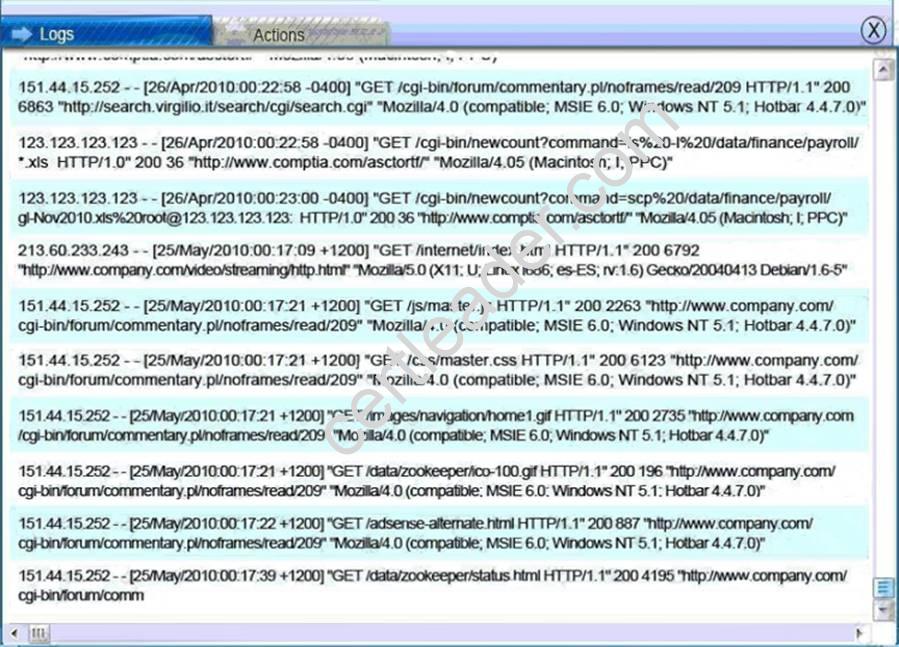
Explanation: Database server was attacked, actions should be to capture network traffic and Chain of Custody.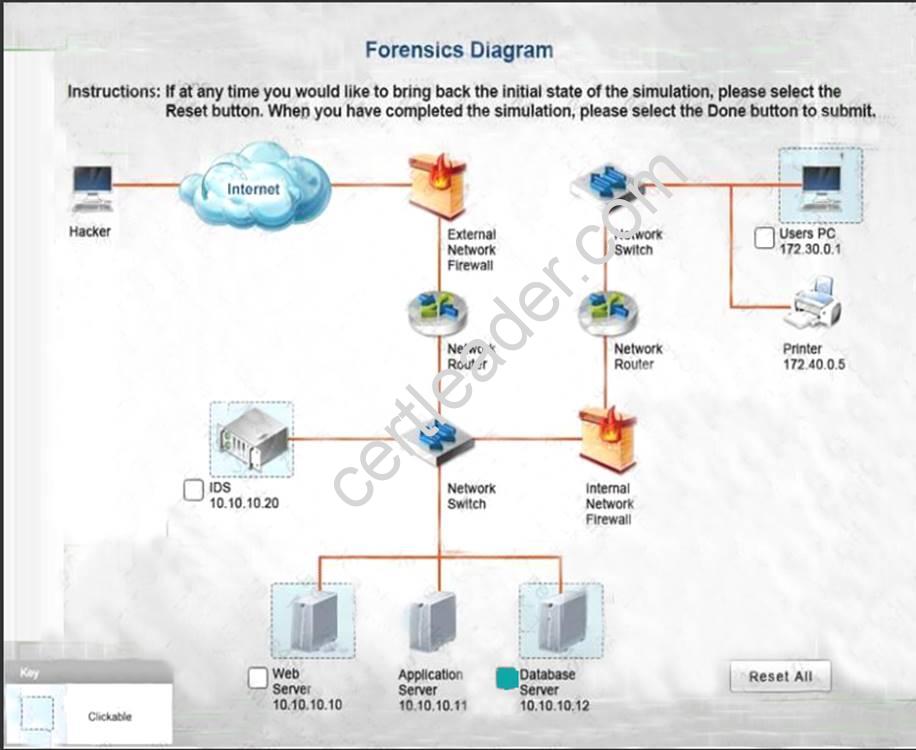
IDS Server Log: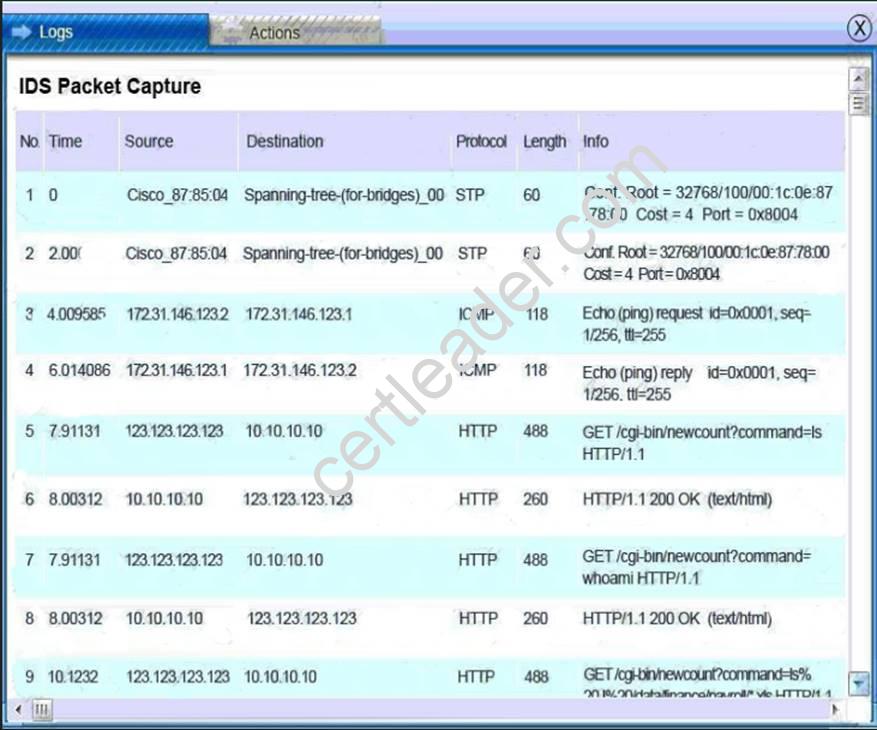
Web Server Log: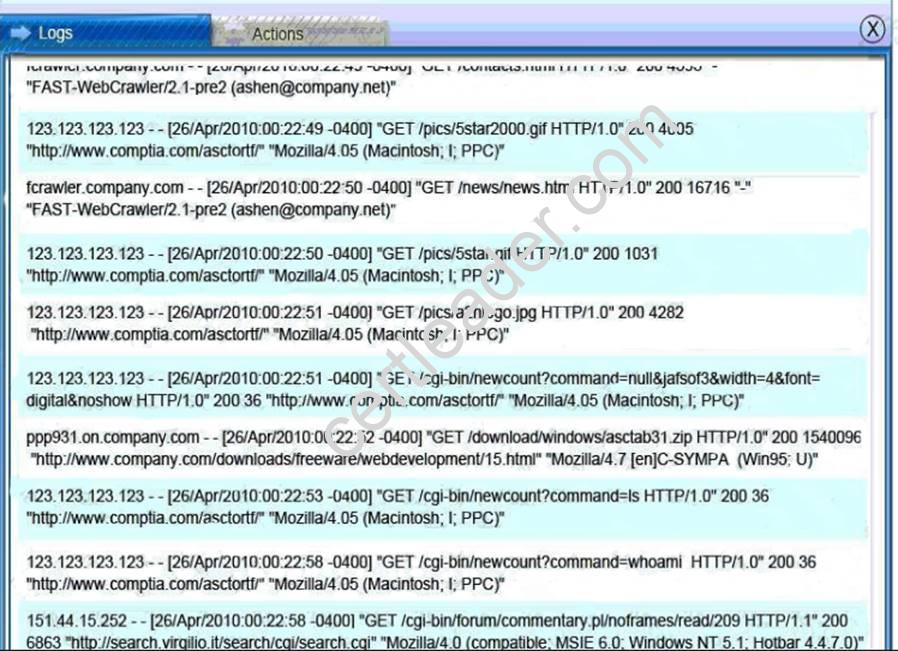
Database Server Log: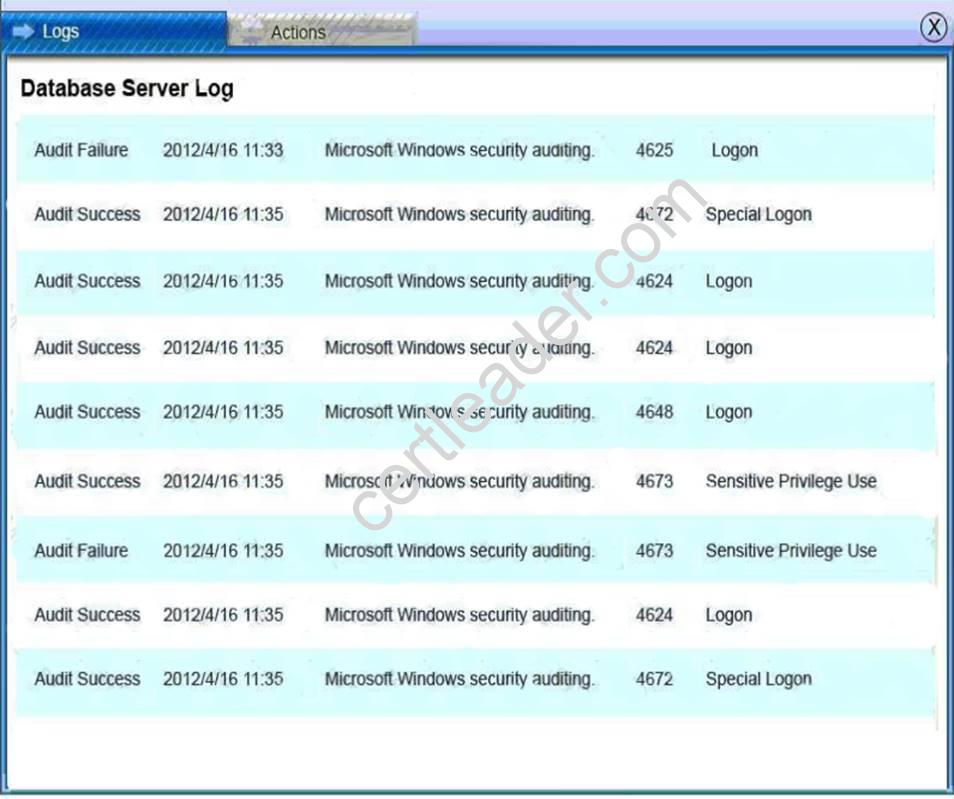
Users PC Log: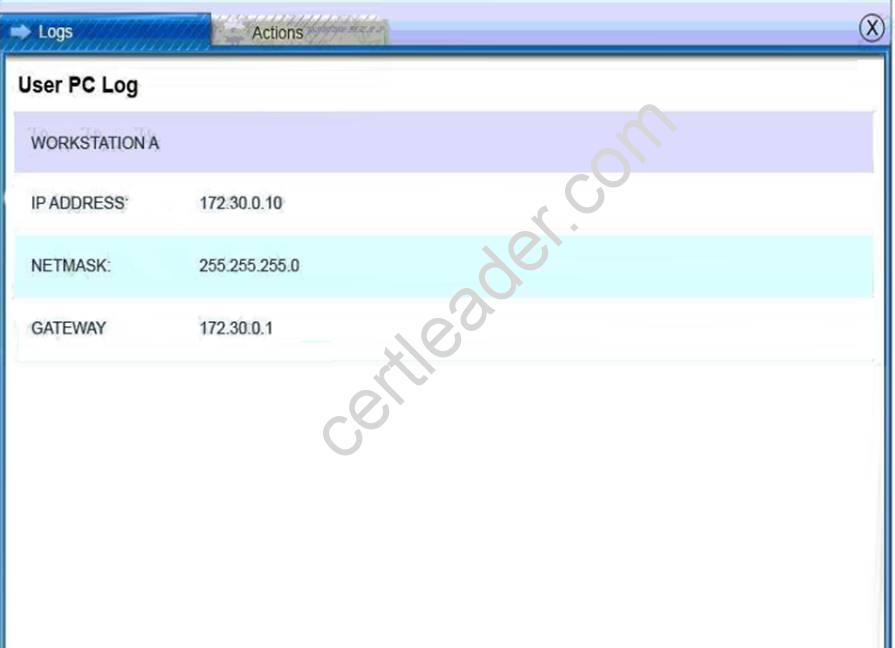
NEW QUESTION 5
Task: Configure the firewall (fill out the table) to allow these four rules: Only allow the Accounting computer to have HTTPS access to the Administrative server.
Only allow the Accounting computer to have HTTPS access to the Administrative server. Only allow the HR computer to be able to communicate with the Server 2 System over SCP.
Only allow the HR computer to be able to communicate with the Server 2 System over SCP. Allow the IT computer to have access to both the Administrative Server 1 and Administrative Server 2
Allow the IT computer to have access to both the Administrative Server 1 and Administrative Server 2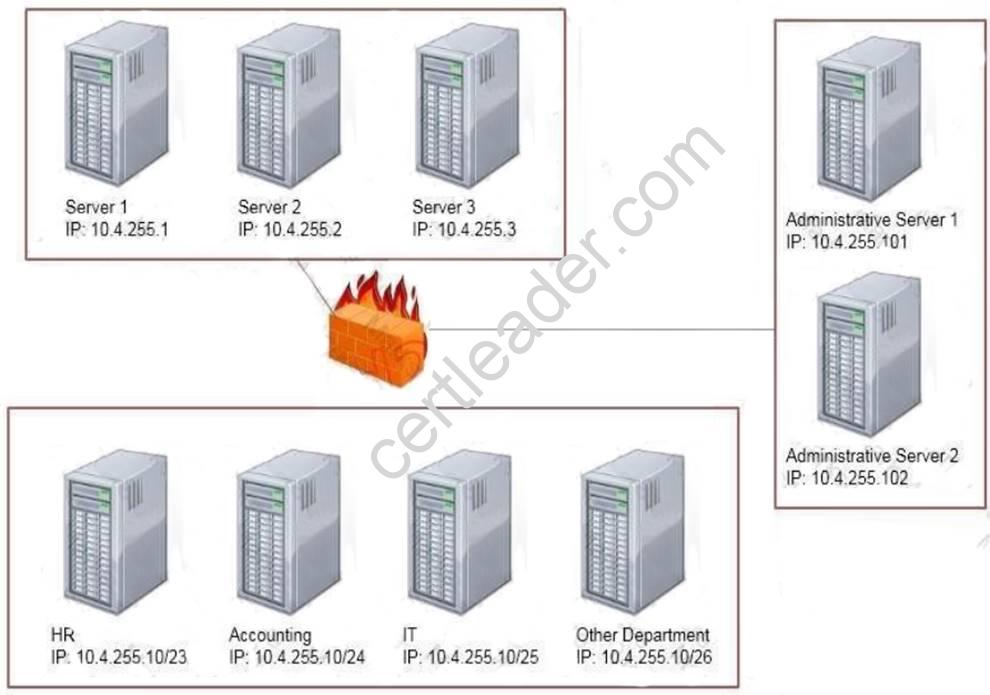
Answer:
Explanation: Use the following answer for this simulation task.
Below table has all the answers required for this question.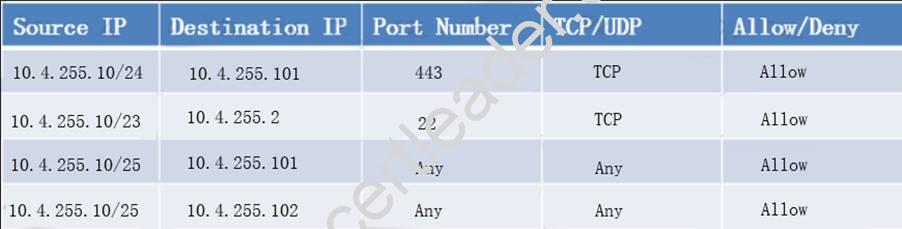
Firewall rules act like ACLs, and they are used to dictate what traffic can pass between the firewall and the internal network. Three possible actions can be taken based on the rule's criteria:
Block the connection Allow the connection Allow the connection only if it is secured
TCP is responsible for providing a reliable, one-to-one, connection-oriented session. TCP establishes a connection and ensures that the other end receives any packets sent.
Two hosts communicate packet results with each other. TCP also ensures that packets are decoded and sequenced properly. This connection is persistent during the session.
When the session ends, the connection is torn down.
UDP provides an unreliable connectionless communication method between hosts. UDP is considered a best-effort protocol, but it's considerably faster than TCP.
The sessions don't establish a synchronized session like the kind used in TCP, and UDP doesn't guarantee error-free communications.
The primary purpose of UDP is to send small packets of information.
The application is responsible for acknowledging the correct reception of the data. Port 22 is used by both SSH and SCP with UDP.
Port 443 is used for secure web connections? HTTPS and is a TCP port.
Thus to make sure only the Accounting computer has HTTPS access to the Administrative server you should use TCP port 443 and set the rule to allow communication between 10.4.255.10/24 (Accounting) and 10.4.255.101 (Administrative server1) Thus to make sure that only the HR computer has access to Server2 over SCP you need use of TCP port 22 and set the rule to allow communication between 10.4.255.10/23 (HR) and 10.4.255.2 (server2)
Thus to make sure that the IT computer can access both the Administrative servers you need to use a port and accompanying port number and set the rule to allow communication between: 10.4.255.10.25 (IT computer) and 10.4.255.101 (Administrative server1)
10.4.255.10.25 (IT computer) and 10.4.255.102 (Administrative server2)
NEW QUESTION 6
An audit reported has identifies a weakness that could allow unauthorized personnel access to the facility at its main entrance and from there gain access to the network. Which of the following would BEST resolve the vulnerability?
- A. Faraday cage
- B. Air gap
- C. Mantrap
- D. Bollards
Answer: C
NEW QUESTION 7
Which of the following is the proper way to quantify the total monetary damage resulting from an exploited vulnerability?
- A. Calculate the ALE
- B. Calculate the ARO
- C. Calculate the MTBF
- D. Calculate the TCO
Answer: A
NEW QUESTION 8
A security technician is configuring an access management system to track and record user actions. Which of the following functions should the technician configure?
- A. Accounting
- B. Authorization
- C. Authentication
- D. Identification
Answer: A
NEW QUESTION 9
Anne, the Chief Executive Officer (CEO), has reported that she is getting multiple telephone calls from someone claiming to be from the helpdesk. The caller is asking to verify her network authentication credentials because her computer is broadcasting across the network. This is MOST likely which of the following types of attacks?
- A. Vishing
- B. Impersonation
- C. Spim
- D. Scareware
Answer: A
NEW QUESTION 10
An organization finds that most help desk calls are regarding account lockout due to a variety of applications running on different systems. Management is looking for a solution to reduce the number of account lockouts while improving security. Which of the following is the BEST solution for this organization?
- A. Create multiple application accounts for each user.
- B. Provide secure tokens.
- C. Implement SSO.
- D. Utilize role-based access control.
Answer: C
NEW QUESTION 11
A security analyst is attempting to break into a client's secure network. The analyst was not given prior information about the client, except for a block of public IP addresses that are currently in use. After network enumeration, the analyst's NEXT step is to perform:
- A. a risk analysis.
- B. a vulnerability assessment.
- C. a gray-box penetration test.
- D. an external security audit.
- E. a red team exercise.
Answer: C
NEW QUESTION 12
Joe notices there are several user accounts on the local network generating spam with embedded malicious code. Which of the following technical control should Joe put in place to BEST reduce these incidents?
- A. Account lockout
- B. Group Based Privileges
- C. Least privilege
- D. Password complexity
Answer: A
NEW QUESTION 13
Which of the following attack types is being carried out where a target is being sent unsolicited messages via Bluetooth?
- A. War chalking
- B. Bluejacking
- C. Bluesnarfing
- D. Rogue tethering
Answer: B
Explanation: Bluejacking is the sending of unsolicited messages over Bluetooth to Bluetooth-enabled devices such as mobile phones, PDAs or laptop computers, sending a vCard which typically contains a message in the name field (i.e., for bluedating or bluechat) to another Bluetooth-enabled device via the OBEX protocol.
NEW QUESTION 14
Which of the following penetration testing concepts is being used when an attacker uses public Internet databases to enumerate and learn more about a target?
- A. Reconnaissance
- B. Initial exploitation
- C. Pivoting
- D. Vulnerability scanning
- E. White box testing
Answer: A
NEW QUESTION 15
When designing a web based client server application with single application server and database cluster backend, input validation should be performed:
- A. On the client
- B. Using database stored procedures
- C. On the application server
- D. Using HTTPS
Answer: C
NEW QUESTION 16
A network administrator at a small office wants to simplify the configuration of mobile clients connecting to an encrypted wireless network. Which of the following should be implemented in the administrator does not want to provide the wireless password or he certificate to the employees?
- A. WPS
- B. 802.1x
- C. WPA2-PSK
- D. TKIP
Answer: A
P.S. Certshared now are offering 100% pass ensure SY0-501 dumps! All SY0-501 exam questions have been updated with correct answers: https://www.certshared.com/exam/SY0-501/ (540 New Questions)