2025 New SY0-501 Exam Dumps with PDF and VCE Free: https://www.2passeasy.com/dumps/SY0-501/
Want to know features? Want to lear more about experience? Study . Gat a success with an absolute guarantee to pass CompTIA SY0-501 (CompTIA Security+ Certification Exam) test on your first attempt.
CompTIA SY0-501 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
An organization wishes to provide better security for its name resolution services. Which of the following technologies BEST supports the deployment of DNSSEC at the organization?
- A. LDAP
- B. TPM
- C. TLS
- D. SSL
- E. PKI
Answer: E
NEW QUESTION 2
An analyst is reviewing a simple program for potential security vulnerabilities before being deployed to a Windows server. Given the following code:
Which of the following vulnerabilities is present?
- A. Bad memory pointer
- B. Buffer overflow
- C. Integer overflow
- D. Backdoor
Answer: B
NEW QUESTION 3
A datacenter recently experienced a breach. When access was gained, an RF device was used to access an air-gapped and locked server rack. Which of the following would BEST prevent this type of attack?
- A. Faraday cage
- B. Smart cards
- C. Infrared detection
- D. Alarms
Answer: A
NEW QUESTION 4
A member of a digital forensics team, Joe arrives at a crime scene and is preparing to collect system data. Before powering the system off, Joe knows that he must collect the most volatile date first. Which of the following is the correct order in which Joe should collect the data?
- A. CPU cache, paging/swap files, RAM, remote logging data
- B. RAM, CPU cach
- C. Remote logging data, paging/swap files
- D. Paging/swap files, CPU cache, RAM, remote logging data
- E. CPU cache, RAM, paging/swap files, remote logging data
Answer: D
NEW QUESTION 5
A systems administrator is attempting to recover from a catastrophic failure in the datacenter. To recover the domain controller, the systems administrator needs to provide the domain administrator credentials. Which of the following account types is the systems administrator using?
- A. Local account
- B. Guest account
- C. Service account
- D. User account
Answer: C
NEW QUESTION 6
An audit has revealed that database administrators are also responsible for auditing database changes and backup logs. Which of the following access control methodologies would BEST mitigate this concern?
- A. Time of day restrictions
- B. Principle of least privilege
- C. Role-based access control
- D. Separation of duties
Answer: D
NEW QUESTION 7
Which of the following strategies should a systems architect use to minimize availability risks due to insufficient storage capacity?
- A. High availability
- B. Scalability
- C. Distributive allocation
- D. Load balancing
Answer: B
NEW QUESTION 8
As part of a new industry regulation, companies are required to utilize secure, standardized OS settings. A technical must ensure the OS settings are hardened. Which of the following is the BEST way to do this?
- A. Use a vulnerability scanner.
- B. Use a configuration compliance scanner.
- C. Use a passive, in-line scanner.
- D. Use a protocol analyzer.
Answer: B
NEW QUESTION 9
Users in a corporation currently authenticate with a username and password. A security administrator wishes to implement two-factor authentication to improve security.
Which of the following authentication methods should be deployed to achieve this goal?
- A. PIN
- B. Security QUESTION NO:
- C. Smart card
- D. Passphrase
- E. CAPTCHA
Answer: C
NEW QUESTION 10
Ann, a user, states that her machine has been behaving erratically over the past week. She has experienced slowness and input lag and found text files that appear to contain pieces of her emails or online conversations with coworkers. The technician runs a standard virus scan but detects nothing. Which of the following types of malware has infected the machine?
- A. Ransomware
- B. Rootkit
- C. Backdoor
- D. Keylogger
Answer: D
NEW QUESTION 11
Which of the following delineates why it is important to perform egress filtering and monitoring on Internet connected security zones of interfaces on a firewall?
- A. Egress traffic is more important than ingress traffic for malware prevention
- B. To rebalance the amount of outbound traffic and inbound traffic
- C. Outbound traffic could be communicating to known botnet sources
- D. To prevent DDoS attacks originating from external network
Answer: B
NEW QUESTION 12
As part of the SDLC, a third party is hired to perform a penetration test. The third party will have access to the source code, integration tests, and network diagrams. Which of the following BEST describes the assessment being performed?
- A. Black box
- B. Regression
- C. White box
- D. Fuzzing
Answer: C
NEW QUESTION 13
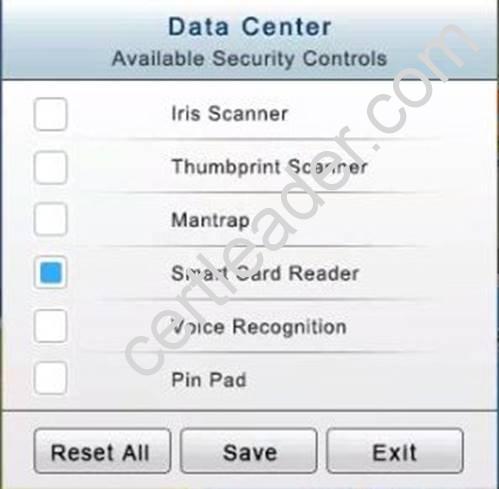
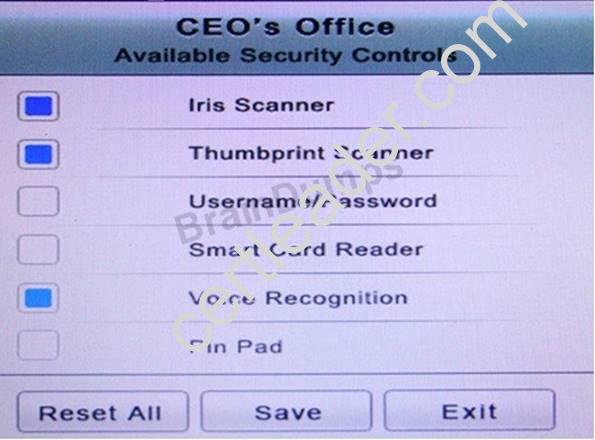
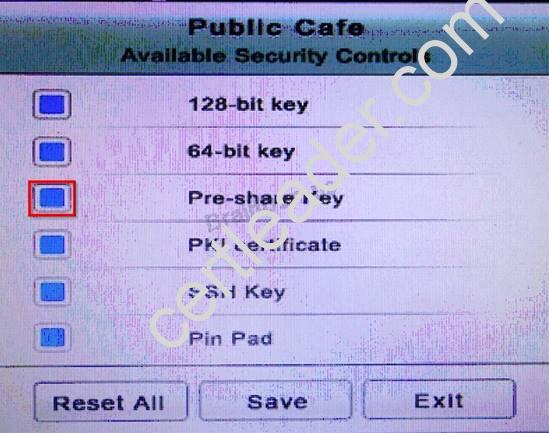
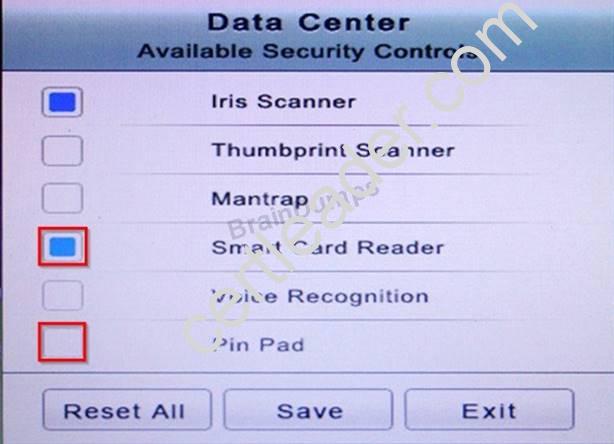
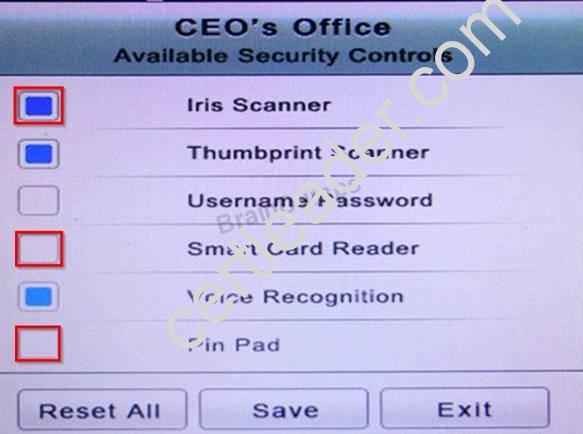
You have just received some room and WiFi access control recommendations from a security consulting company. Click on each building to bring up available security controls. Please implement the following requirements:
The Chief Executive Officer's (CEO) office had multiple redundant security measures installed on the door to the office. Remove unnecessary redundancies to deploy three-factor authentication, while retaining the expensive iris render.
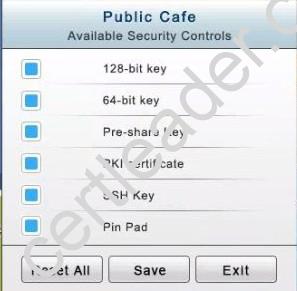
The Public Cafe has wireless available to customers. You need to secure the WAP with WPA and place a passphrase on the customer receipts.
In the Data Center you need to include authentication from the "something you know" category and take advantage of the existing smartcard reader on the door.
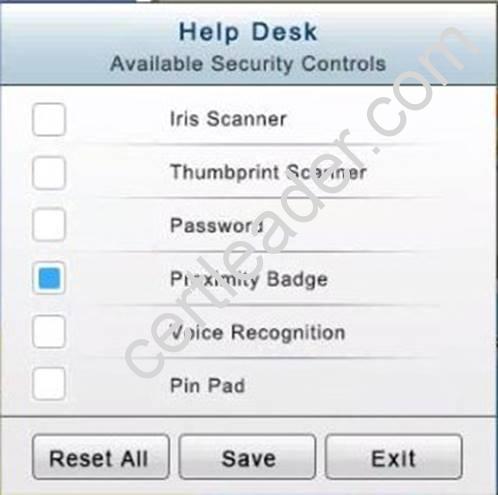
In the Help Desk Office, you need to require single factor authentication through the use of physical tokens given to guests by the receptionist.
The PII Office has redundant security measures in place. You need to eliminate the redundancy while maintaining three-factor authentication and retaining the more expensive controls.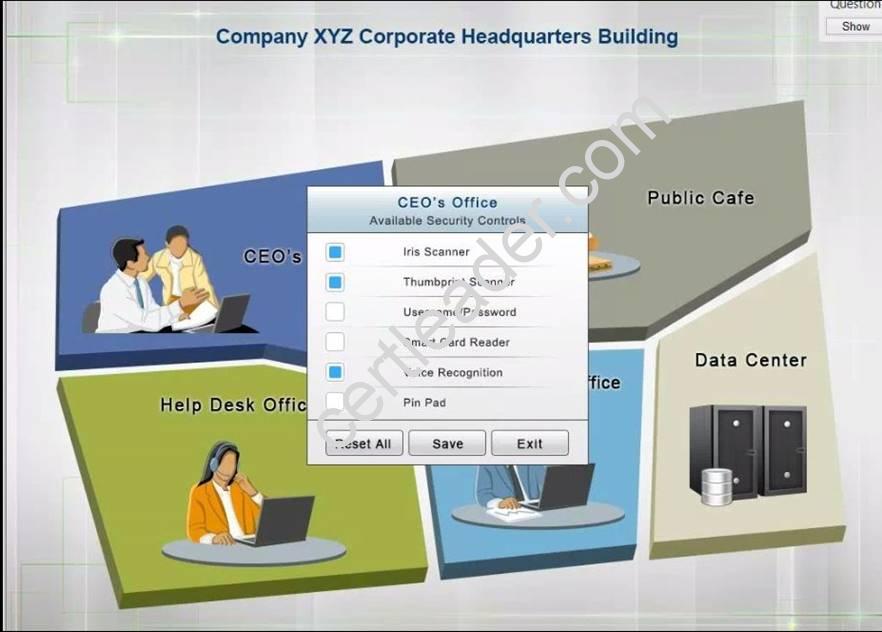
Instructions: The original security controls for each office can be reset at any time by selecting the Reset button. Once you have met the above requirements for each office, select the Save button. When you have completed the entire simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.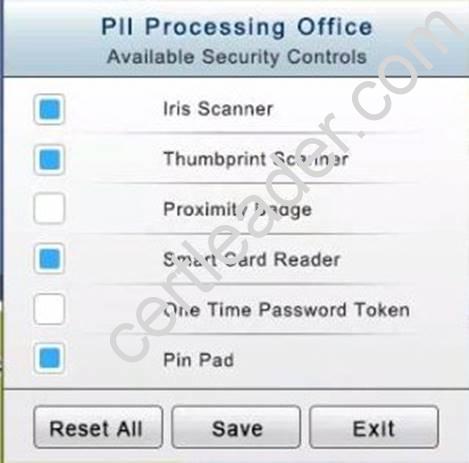
Answer:
Explanation:
Solution as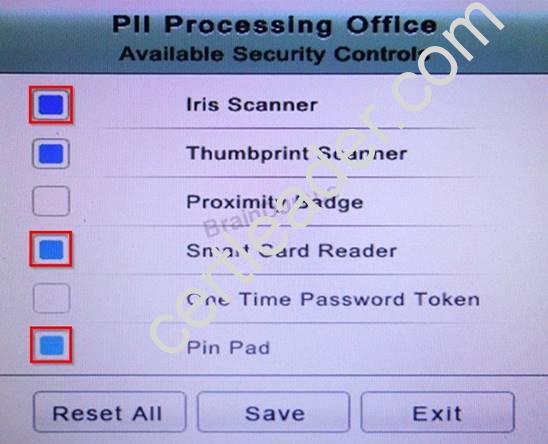
NEW QUESTION 14
Security administrators attempted corrective action after a phishing attack. Users are still experiencing trouble logging in, as well as an increase in account lockouts. Users' email contacts are complaining of an increase in spam and social networking requests. Due to the large number of affected accounts, remediation must be accomplished quickly. Which of the following actions should be taken FIRST? (Select TWO)
- A. Disable the compromised accounts
- B. Update WAF rules to block social networks
- C. Remove the compromised accounts with all AD groups
- D. Change the compromised accounts' passwords
- E. Disable the open relay on the email server
- F. Enable sender policy framework
Answer: EF
Explanation: Sender Policy Framework (SPF) is a simple email-validation system designed to detect email spoofing by providing a mechanism to allow receiving mail exchangers to check that incoming mail from a domain comes from a host authorized by that domain's administrators. n a Small Business Server environment, you may have to prevent your Microsoft Exchange Server-based server from being used as an open relay SMTP server for unsolicited commercial e-mail messages, or spam.
You may also have to clean up the Exchange server's SMTP queues to delete the unsolicited commercial email messages.
If your Exchange server is being used as an open SMTP relay, you may experience one or more of the following symptoms:
The Exchange server cannot deliver outbound SMTP mail to a growing list of e-mail domains. Internet browsing is slow from the server and from local area network (LAN) clients.
Free disk space on the Exchange server in the location of the Exchange information store databases or the Exchange information store transaction logs is reduced more rapidly than you expect.
The Microsoft Exchange information store databases spontaneously dismount. You may be able to manually mount the stores by using Exchange System Manager, but the stores may dismount on their own after they run for a short time. For more information, click the following article number to view the article in the Microsoft Knowledge Base.
NEW QUESTION 15
Which of the following locations contain the MOST volatile data?
- A. SSD
- B. Paging file
- C. RAM
- D. Cache memory
Answer: D
NEW QUESTION 16
An analyst wants to implement a more secure wireless authentication for office access points. Which of the following technologies allows for encrypted authentication of wireless clients over TLS?
- A. PEAP
- B. EAP
- C. WPA2
- D. RADIUS
Answer: A
Explanation: EAP by itself is only an authentication framework.
PEAP (Protected Extensible Authentication Protocol) fully encapsulates EAP and is designed to work within a TLS (Transport Layer Security) tunnel that may be encrypted but is authenticated. The primary motivation behind the creation of PEAP was to help correct the deficiencies discovered within EAP since that protocol assumes that the communications channel is protected. As a result, when EAP messages are able to be
discovered in the “clear” they do not provide the protection that was assumed when the protocol was originally authored.
PEAP, EAP-TTLS, and EAP-TLS “protect” inner EAP authentication within SSL/TLS sessions.
100% Valid and Newest Version SY0-501 Questions & Answers shared by Exambible, Get Full Dumps HERE: https://www.exambible.com/SY0-501-exam/ (New 540 Q&As)